HTX(Houbi) Exchange Hack Breakdown
Introduction
Hack discovered
On the 24th of September 2023, at approximately 6:00 am EST the Houbi (newly named HTX) experienced a security breach resulting in the unauthorized transfer of 5,000 Eth, equivalent to 8 million USD.
White hat reward offered
Founder of Tron, and Houbi investor Justin Sun officially disclosed this incident on the the 25th of September 2023 with an offer of 5% ($400,000 USD) of the stolen amount as a white hat reward.
“ We are willing to offer 5% of the stolen amount (400,000 USD) as a white hat reward to encourage the hacker to return the stolen funds. If the hacker returns the funds, we will also hire them as a security white hat advisor for HTX.” - Justin Sun.
Hacker returned the money and took white had offer
Around 5:00 pm EST on Sunday evening, the suspected Huobi hot wallet executed a transfer, sending 4,999 Ether, equivalent to approximately $7.9 million USD, to an address without any previous transaction history.
Blockscope Findings
After conducting a thorough examination of the hack, Blockscope was able to find entry points involving the hacker address, and the HTX hot wallet that initiated this transaction as well as the transaction hash involved.
Our research has substantiated that the aggregate loss amounts to 4,999 ETH, equivalent to a valuation of $7.9 million USD was returned and the hacked claimed the white hat reward.
Investigation
Step 1 - Transaction Decoder
In order to begin our investigation, we will be leveraging the specialized investigative tools offered by Blockscope. Specifically, our initial endeavor will involve employing Blockscope’s Transaction Decoder. This tool will play a pivotal role in dissecting the transaction, unveiling pertinent addresses involved in the exploit. Blockscope’s Transaction Decoder, empowers users to see who was involved in the exploit and breakdown how the hack happened.
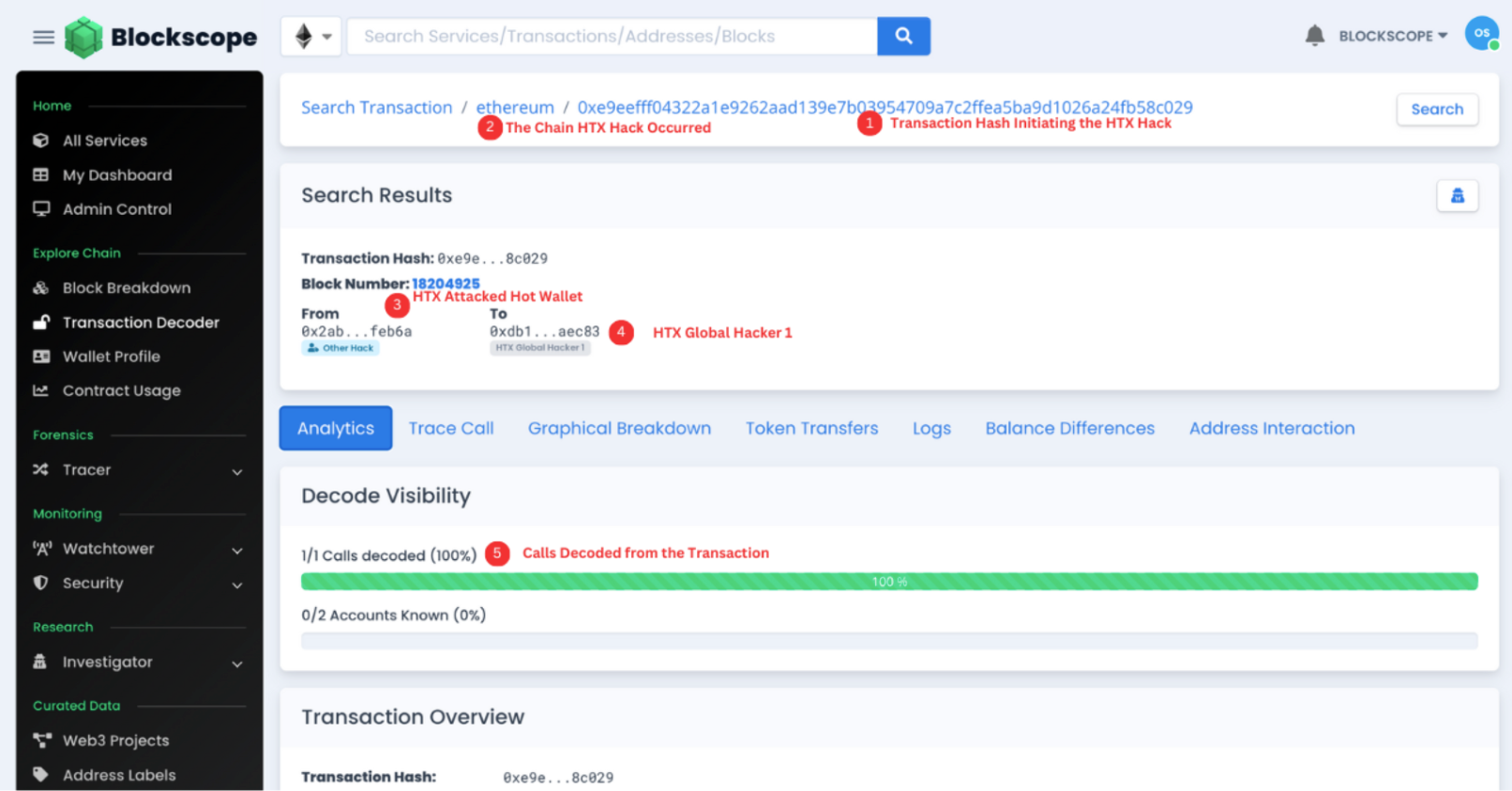
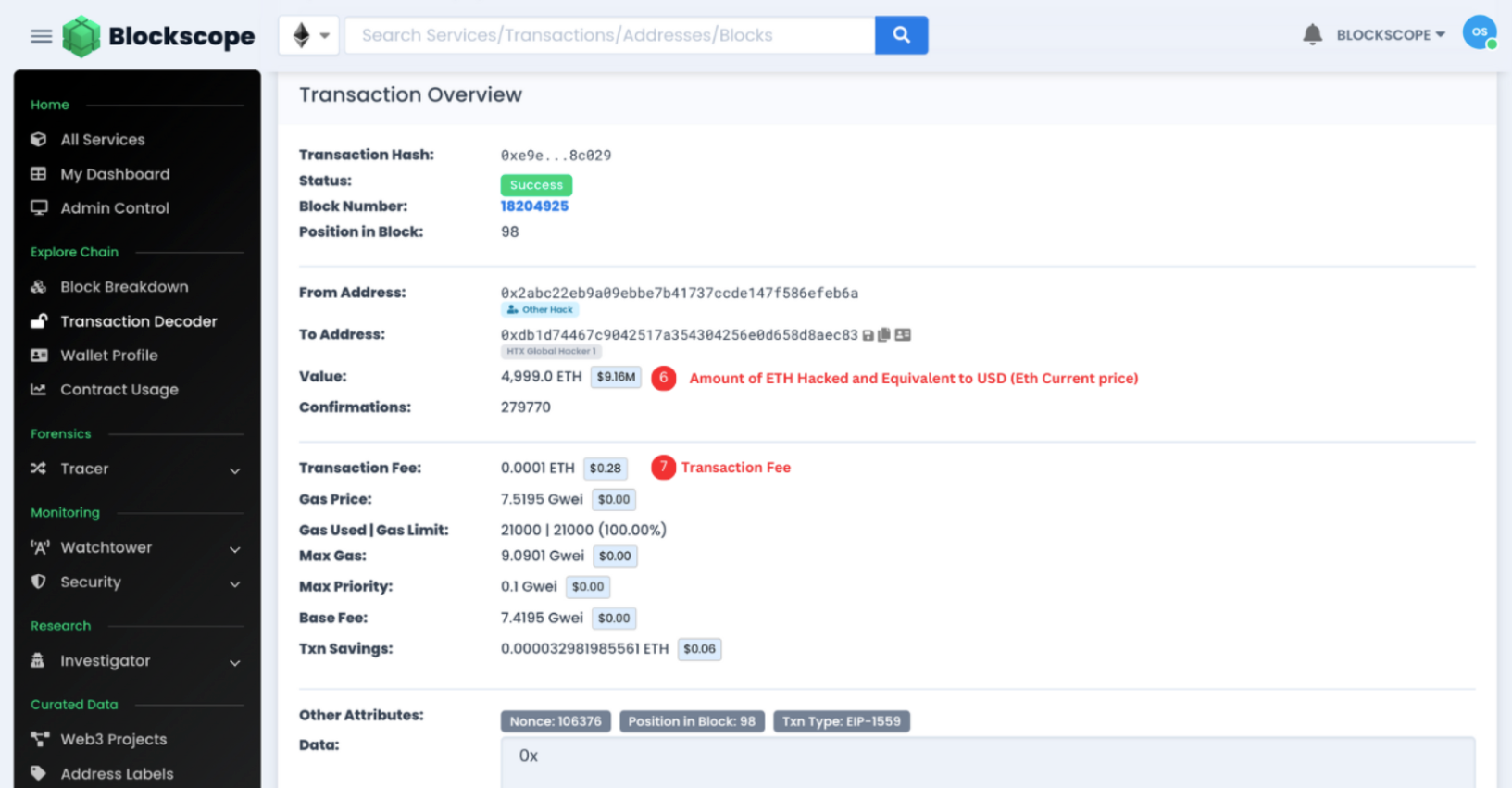
Through a quick examination of the decoded transaction, we have successfully pinpointed the compromised HTX Hot wallet, as well as the designated recipient wallet utilized by the HTX Hacker to receive the 4,999 ETH.
These wallets are as follows
0x2abc22eb9a09ebbe7b41737ccde147f586efeb6a (Attacked HTX Hot wallet)
0xdb1d74467c9042517a354304256e0d658d8aec83 (HTX Global Hacker 1)
Step 2 - Tracer
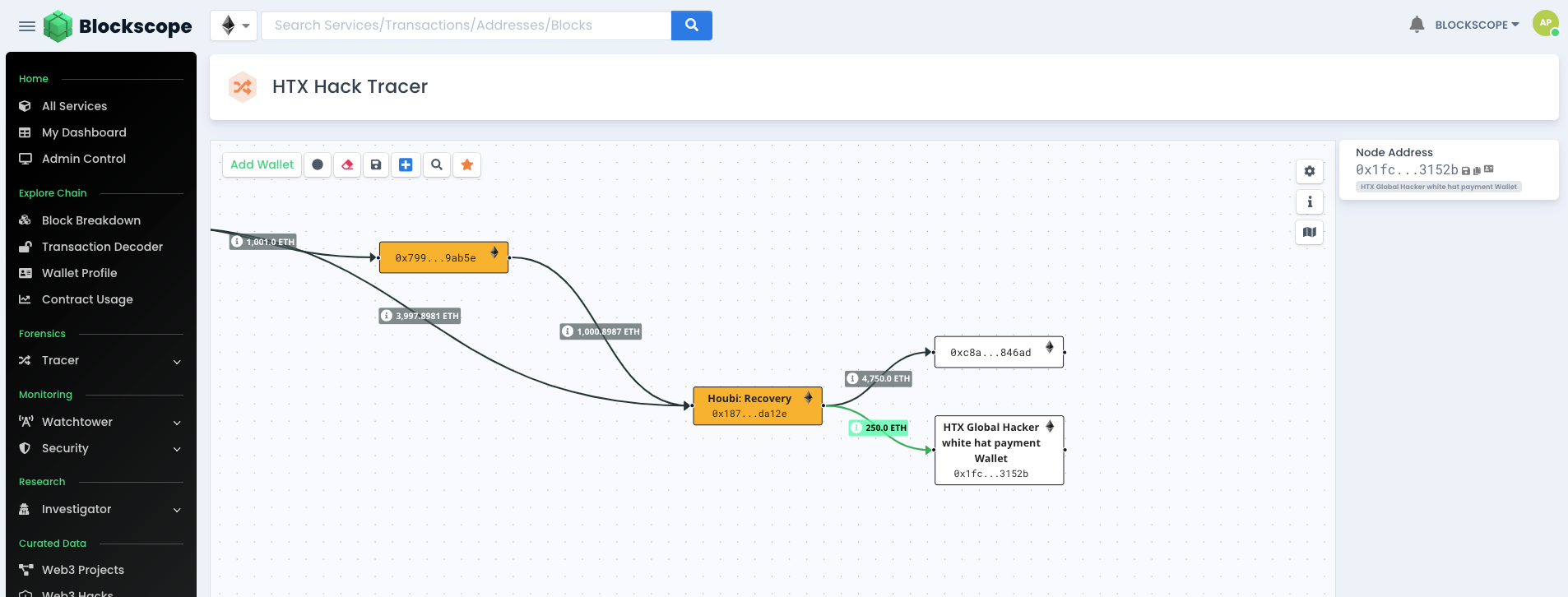
Following our successful identification of these addresses, we are can now do a deep dive on he addresses involved by using Blockscope’s Tracer Tool. This tool is enables users to track and visualize the movements of funds across various wallets on the blockchain. Tracer equips users with a comprehensive view of token flow, enabling the identification of potentially suspicious transactions, and thereby enhancing their investigative capabilities.
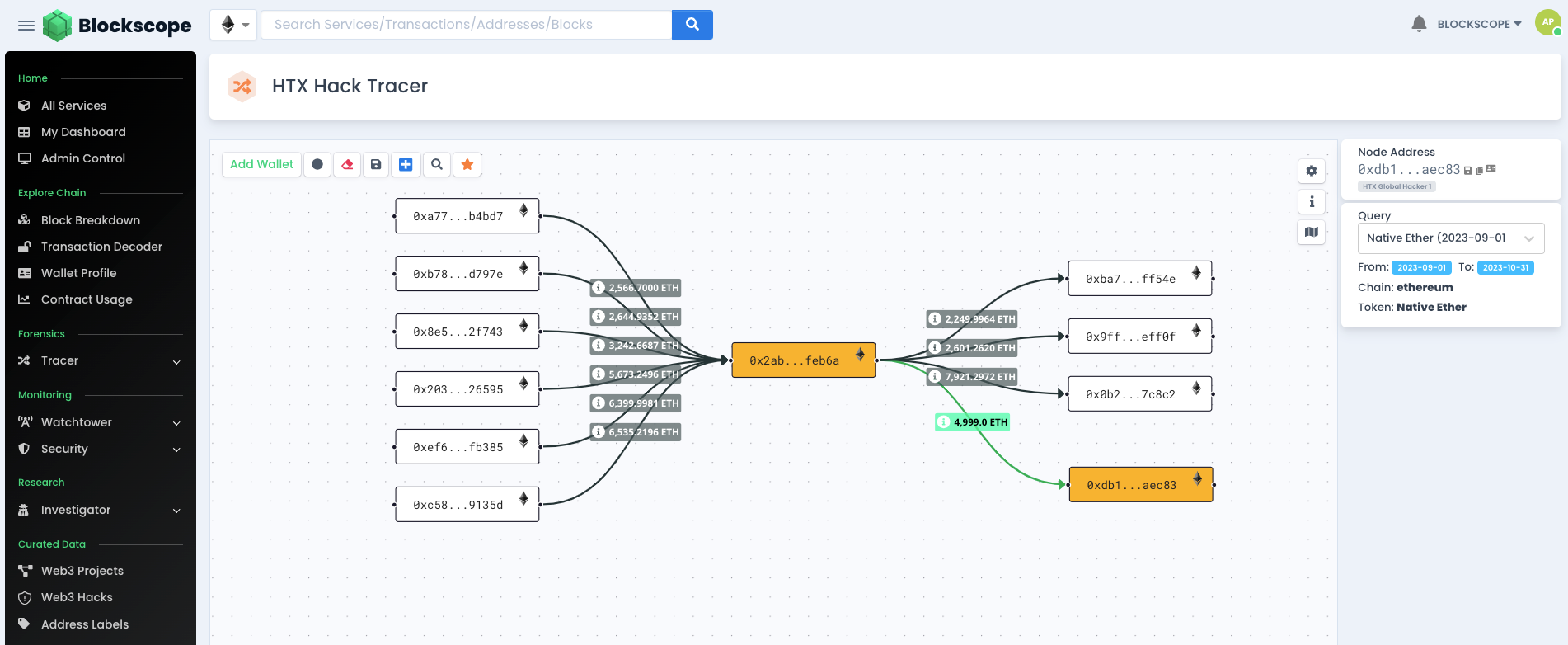
Right away, we have verified the outflow of the reported 4,999 ETH from 0x2abc22eb9a09ebbe7b41737ccde147f586efeb6a (The compromised HTX hot wallet) to 0xdb1d74467c9042517a354304256e0d658d8aec83 (HTX Global Hacker 1).
Lets see where the funds went from here. Further expanding on the Hackers wallet shows us he initially moved 1001 ETH to a new wallet. But eventually moved it all to the Houbi Recovery wallet
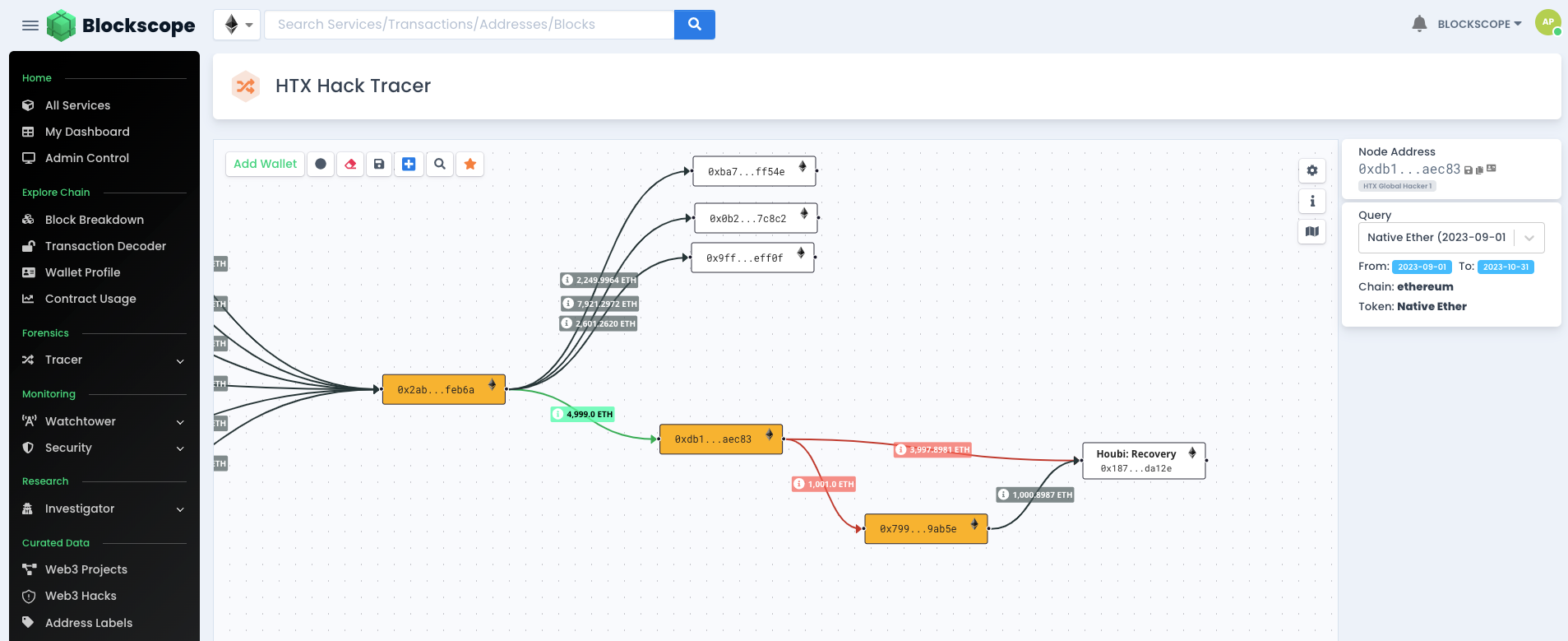
Next expanding on the Houbi Recovery Wallet, we can see 5% payment of 250 ETH was made to the white hacker's wallet and the remaining funds were moved out by Houbi to what we can assume is another one of their accounts.
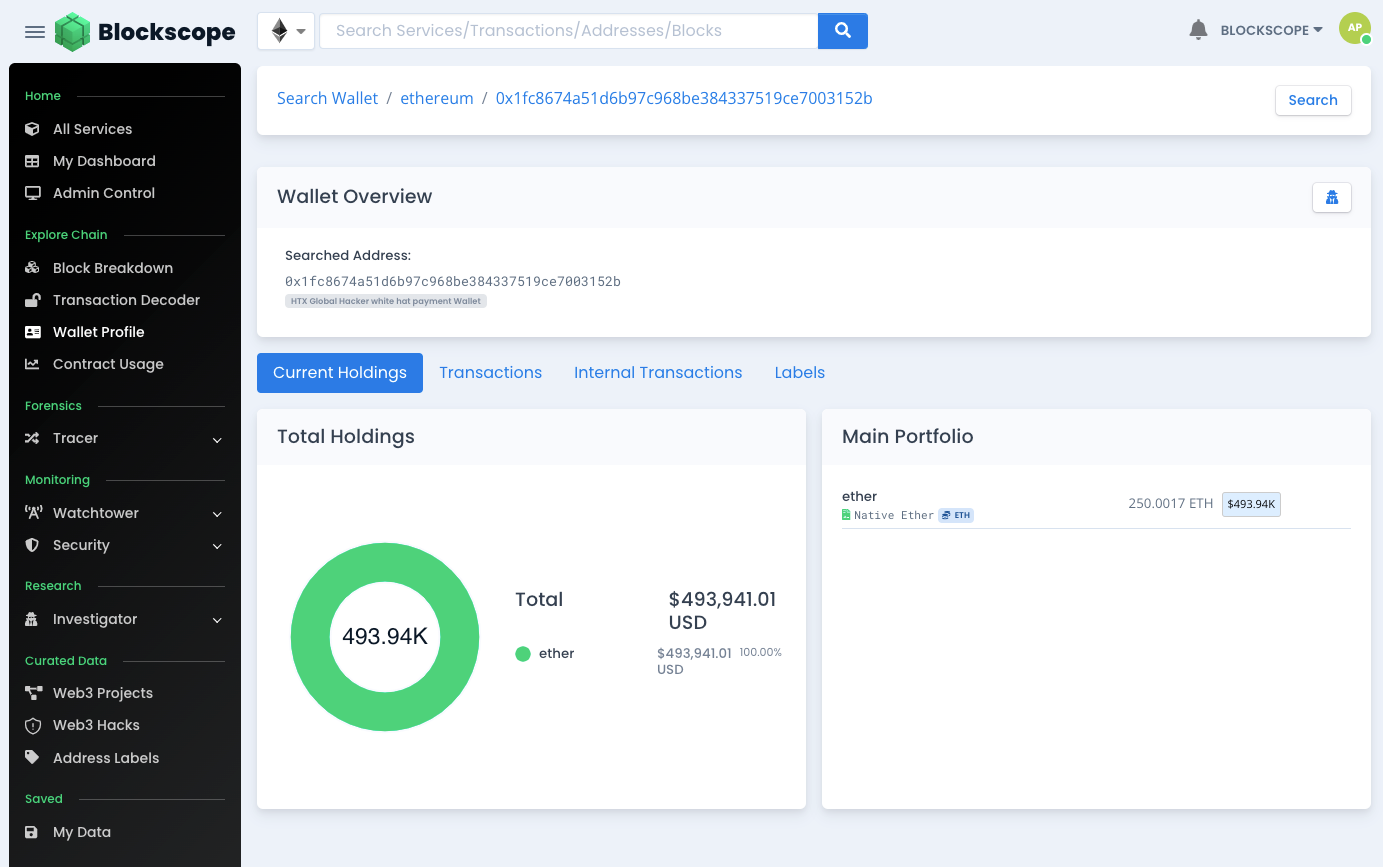
Step 3 - Wallet Profiler
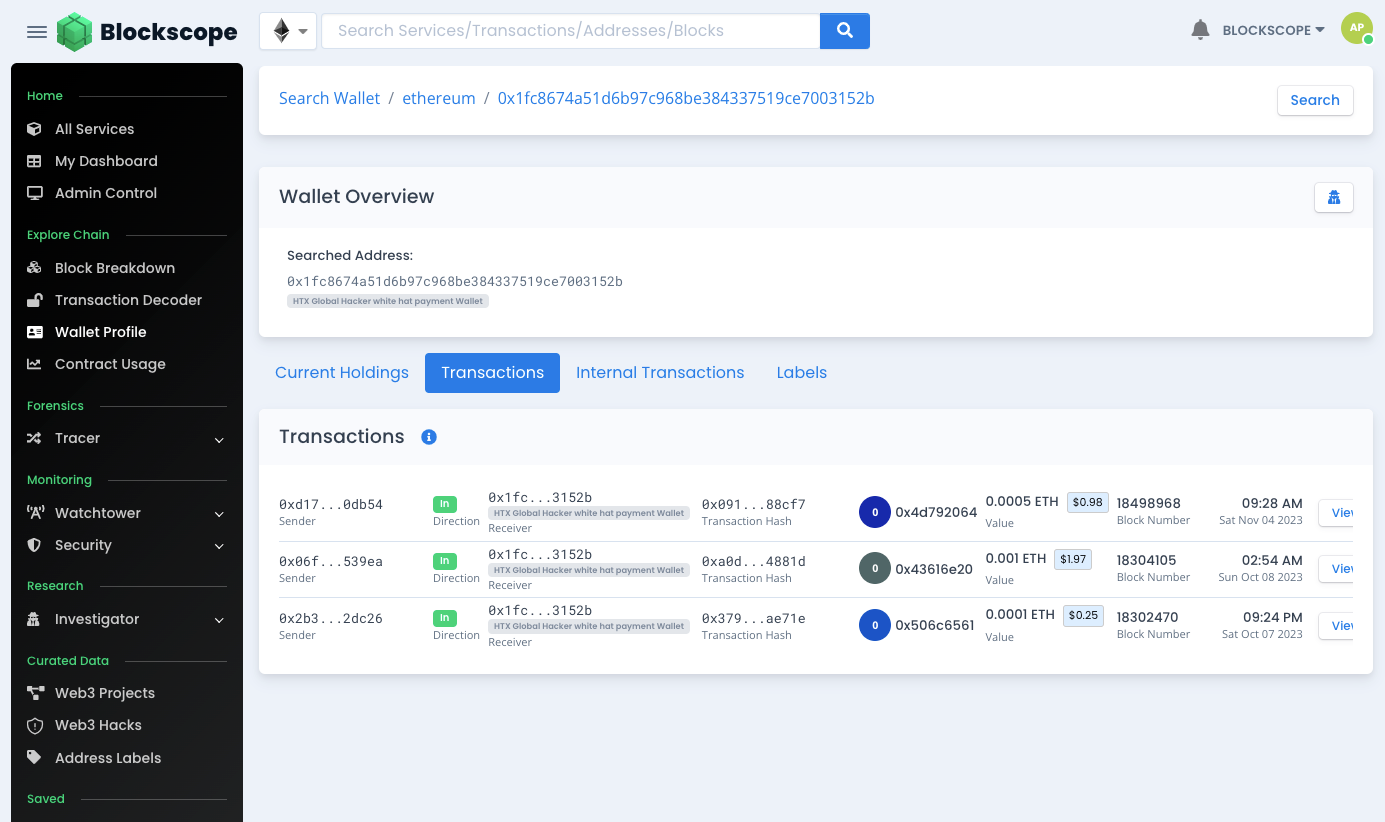
We know the address of the account that received the reward funds of 250 ETH. Using Blockscope's Wallet Profiler tool confirms 2 things, the funds are still there and the user has not triggered any transactions moving funds out.
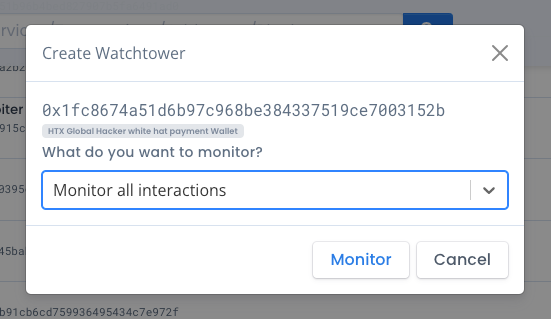
Step 4 - Monitor with Watchtower
We have the opportunity to see how these funds move into the future. We will use the watchtower tool and set up monitoring on this wallet. If any of these funds move, we will know in realtime!
Summary
The hacker was sucessfully able to steal funds from one of HTX(Houbi)'s Hot Wallets. They then moved the funds back into Houbi Recovery wallet. As a result, they earned 5% about 250 ETH worth 400,000 USD. These funds are still in their wallet, we've set up monitoring so if the funds move again, we'll know in realtime!